Why use a VPN?
VPN stands for Virtual Private Network. It establishes a tunnel within a so-called “insecure” network such as the internet.
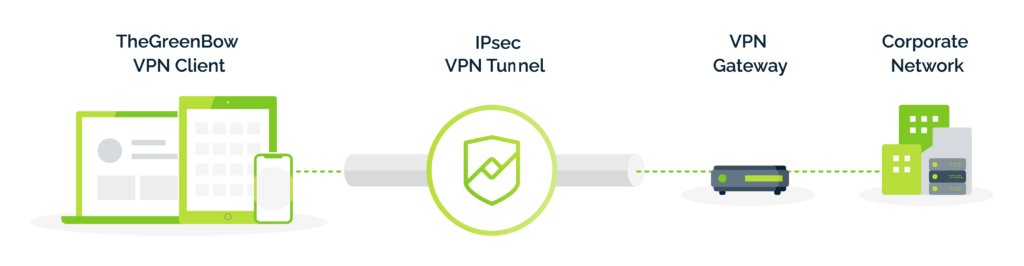
To ensure that data exchanges are secure, a VPN performs three functions:
- Authentication using a key to make sure that the devices are authorized to communicate with each other
- Data encryption to guarantee the confidentiality of exchanges
- Data integrity to ensure that data has not been tampered with
Discover the full range of TheGreenBow VPN Clients
We offer the most reliable and versatile range of VPN clients on the market for needs as varied as protecting connections while telecommuting or with connected objects, or even securing data exchanges within a network handling critical communications: they are interoperable with any IPsec or OpenVPN gateway, work with any type of network (Wi-Fi, 3G, 4G, 5G, satellite, etc.), are designed to integrate into any public key infrastructure (PKI) and to be deployed on a large scale.
Our VPN clients are available for Windows, Linux, Android, iOS, and macOS. We offer a 30-day free trial to let you discover all their features.
Windows Quantum-SafeRead more |
Windows StandardRead more |
Windows EnterpriseRead more |
Windows Enterprise CertifiedRead more |
|
|---|---|---|---|---|
| Protocols | ||||
| Open VPN | - | |||
| IPsec IKEv1 | - | - | - | |
| IPsec IKEv2 | ||||
| IPv6 support | ||||
| Cryptography | ||||
| DES, 3DES, AES CBC/CTR/GCM 128-192, MD5, SHA-1, DH 1-2 & 5 | - | - | - | |
| AES CBC/CTR/GCM 256-512, SHA-2, DH 14-20 | ||||
| Advanced cryptography (SHA-2 384/512, DH 21+28) | - | |||
| Post-Quantum algorithms | - | - | - | |
| Authentication | ||||
| Pre-shared key, EAP, Certificates | ||||
| Tokens and smart cards | ||||
| Advanced authentications (Brainpool) | - | |||
| Certificate in the OS certificate store | - | - | - | |
| Tunnel | ||||
| All traffic through the tunnel | ||||
| Multiple tunnels | ||||
| Service continuity | ||||
| DPD (Dead Peer Detection) | ||||
| Redundant gateway | - | |||
| Deployment | ||||
| Silent installation and configuration | ||||
| Control software from the command line | - | |||
| Advanced features | ||||
| Always-on (permanent connection) | - | - | - | |
| Trusted network detection | - | - | - | |
| Filtering Mode | - | - | - | |
| Endpoint compliance | - | - | - | |
| Compliance with ANSSI recommendations | ||||
| EAL3+ Common Criteria certification from ANSSI | - | - | - | |
| Compatibility with IPsec DR referential | - | - | ||
| * N/A - Not applicable | ||||
| Test Buy | Test Buy | Test Buy | ||

